Filtering e-mail traffic
Ghent University provides extensive filtering of the e-mail traffic, with the aim of keeping unwanted and dangerous e-mails out of your inbox. In order to give the user insight in to which e-mails are being blocked and the possibility to quickly respond to false positives, we will allow the unwanted mail to flow straight to the "Junk E-Mail" folder of your mailbox. This way you can check for yourself what is being filtered. However, be very careful when opening mail in the Junk E-Mail folder and only consult mail that you expected and clearly recognize.
Scanning and filtering
Ghent University provides scanning and filtering of incoming mail. Because e-mail offers no guarantees about the identity of the sender, it is easy to forge (senders of) e-mails and use it to distribute malicious content. This makes e-mail the favorite medium for hackers, phishers or other individuals with bad intentions. Unfortunately, many serious security incidents start with opening apparently legitimate links or trustworthy looking attachments, or following instructions from known (but falsified) correspondents. This means that Ghent University has to take the necessary measures to prevent this type of mail traffic as much as possible.
A first filtering consists of marking known unwanted e-mails, or known senders of unwanted e-mails. The "fingerprint" of such mails or the IP addresses of senders are automatically shared over the Internet, allowing us to immediately classify mails or senders that are already flagged as untrustworthy by others.
For some public mail providers such as Gmail and Yahoo, this approach is insufficient. Both platforms offer everyone the possibility to (anonymously) create an e-mail address, and they are therefore heavily used by actors with bad intentions, who in this way can quickly vary the e-mail addresses they use for their activities. Flagging all of Gmail or Yahoo isn't an option, of course, and the variations also make using "fingerprints" less effective, so here we're working based on the content of the mail. Thanks to statistical analysis (bayesian inference), we can still identify unwanted mail quite accurately on the basis of the vocabulary used in the mail.
Virus scanner and measures against spoofing
Attachments naturally go through a virus scanner, which also works on a database of known malware that is kept up-to-date. But even that is not enough because many new variants appear every day. Therefore, all attachments and most links (which can also harbor malware) are opened again in a safe, virtual environment, to detect what they do once opened. In this way, even new and unknown malware can be detected before it ends up in a mailbox.
Finally, we combat "spoofing", the falsification of senders, by using mechanisms (SPF, DKIM, DMARC). Companies and institutions can indicate which e-mail systems are thrustworthy for e-mails with their domain name as sender. E-mails that come from elsewhere, or do not have a valid "stamp" from the mail administrator, will also be marked as suspicious. Not all e-mail domains use this system, but we use it when available and we also use this for the ugent.be domain to prevent anyone from posing as a UGent user.
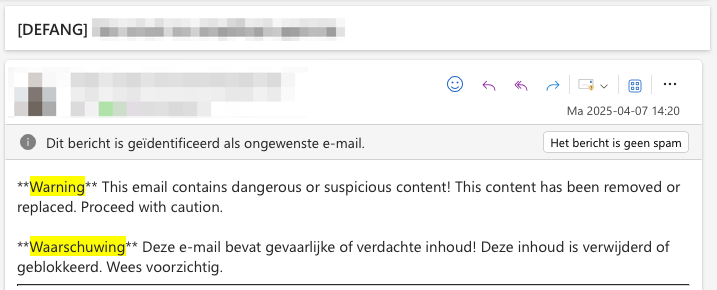
Defang: harmful attachments and links are removed
Harmful attachments and links are removed from incoming e-mails without blocking the e-mail itself, which simply ends up in the 'Junk e-mail' folder.
A warning is also placed at the top of such a 'defanged' e-mail:
Check your "junk mail" folder
We place all suspicious or unwanted e-mail in the "Junk e-mail" folder of your mailbox and only withhold mail that we determine with certainty to be dangerous (virus, ransomware). So it is highly recommended to check that junk mail folder occasionally, because no filtering mechanism is 100% error-free. But treat everything you find in this folder with the utmost caution. If you see strange or unexpected messages, you can assume that they are fake! Only consult mail that you clearly recognize and already expected and keep in mind that malware can be presented in mails from known correspondents or even in mail conversations in which you have already been involved.